Every day thousands of people suffer theft of their smartphones or complain of having lost it. According to research cited by Lookout, a software house that develops anti-theft solutions for mobile devices, 16% of thefts occur in restaurants, 11% in bars, nightclubs, or in the workplace, 6% on public transport.
Even more users, however, report the loss of their precious smartphones. Precious, often, not so much for its economic value but for the type and quantity of personal data it holds.
Realizing that you have lost your mobile phone or realize that it has been stolen can be something dramatic today, especially if the information of great importance to your profession or business was stored in the mobile device.
Find your lost or stolen cell phone with an anti-theft app.
For the various mobile devices, some applications allow you to find the lost or stolen mobile phone.
Their presence on your phone or tablet can make a difference in finding your lost or stolen mobile device.
It is certainly possible to find the lost or stolen phone with the IMEI code (see below). If you want to drastically increase the chances of getting your hands back on your mobile device, installing and configuring an anti-theft app proves decisive.
Anti-theft apps try to determine where the mobile phone or tablet is by checking their GPS coordinates. In the presence of such applications, the mobile device can be managed remotely, and the necessary functions can be activated to receive the GPS coordinates that indicate the positioning of the device.
On Android, the application that Google offers is called Android Device Manager.
By connecting with this page, you can then know your mobile device’s location and manage it remotely by making it ring, blocking it, or completely deleting its content so that it cannot fall prey to malicious people or otherwise unauthorized persons.
However, the big limitation of this application is that it does not offer support for administering the mobile device via SMS. In other words, your data connection (or Wi-Fi) must be active for it to beAndroid Device Manager can function properly.
Next to the Android device manager, we suggest installing and using Cerberus, an app that can be downloaded for free from Google Play.
After a short trial period, if you want to continue using Cerberus, you will have to pay the “one-off” amount of 4.99 euros, a modest outlay that amply justifies the level of peace of mind you will enjoy after installation and the configuration of the anti-theft app.
Among other things, Cerberus allows you to simultaneously protect up to three mobile devices with the same account.
Cerberus brings with it numerous advantages:
– if the lost or stolen mobile phone is connected to the Internet (data connection or Wi-Fi active), it is possible to log in to the cerberusapp.com site from any computer (using personal credentials) and send commands from the web interface
– if the lost or stolen mobile phone is not connected to the Internet, commands can be sent via SMS using any other phone (it does not even need to be a smartphone). The list of available commands is sent by e-mail when Cerberus is first installed.
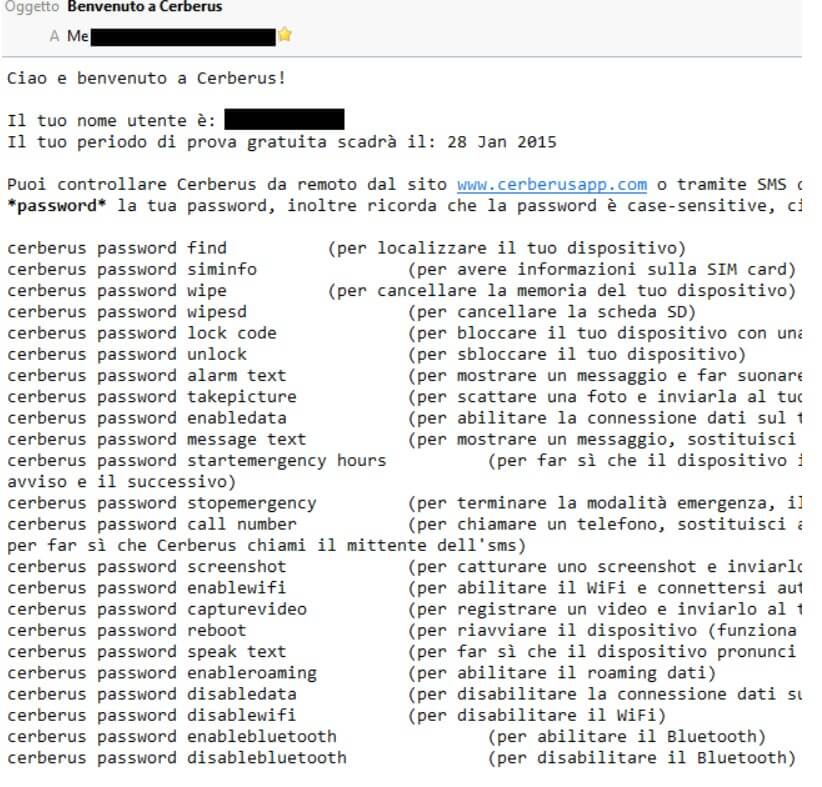
The commands made available by Cerberus and can be sent remotely to your device allow you to locate your smartphone or tablet/phablet, to read the SIM data, to delete the stored data, to activate the data connection on the device, to take a photo of the person using the device, to record a video and send it to their e-mail address, to make the phone ring, to have a sentence pronounced in a synthesized voice and much more.
Due to Android’s limitations, Cerberus cannot force the activation of the GPS module remotely if disabled. On previously rooted Android smartphones ( Install Android ROM and update to the latest version ), however, you can do this by installing Cerberus as a system app (see this page ).
Here are three different ways to install Cerberus as a system app on Android.
The Cerberus authors point out that their app also has a “third head” (from the well-known Greek mythology monster). It can perform actions even automatically when certain conditions occur.
When, for example, the SIM card is changed, Cerberus can send an alert via e-mail and SMS together with the new card’s data. Similarly, Cerberus can send the photo of the alleged thief when an incorrect unlock code is entered.
To grant Cerberus “the powers” to remotely block the device or delete the data, it must necessarily be granted the appropriate rights ( Device administration ).
Lookout is certainly a valid app, which automatically saves the mobile device’s position even when the battery is low before it is completely discharged and sends an e-mail with the face of anyone who enters the wrong unlock code five times in a row.
Find lost or stolen mobile phone with IMEI code.
It is called IMEI, acronym for International Mobile Equipment Identity, that code allows you to uniquely identify a mobile terminal connected to the telephone network.
The indication of the IMEI code is visible immediately under the mobile device’s battery or on the packaging that contained the product.
Alternatively, it can be viewed at any time by entering the code * # 06 # on the phone.
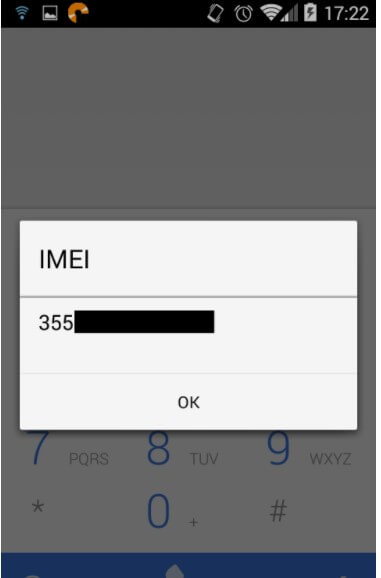
The IMEI code is associated with the SIM card as soon as the user turns on the phone, and it automatically connects to the mobile network.
Since when the SIM has to be replaced, the same IMEI will be associated with another card. The telephone operator will trace the user’s identification data who is using the mobile device.
Therefore, in the event of theft, you can submit a report to the police, taking care to specify the correct IMEI code.
If you cannot trace the IMEI of your phone, you can – in the case of Android devices – connect to this Google page and click on the Android item.
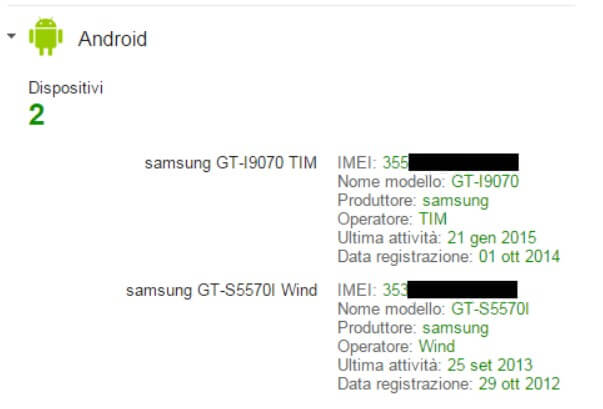
This will take you to the complete list of Android smartphones associated with your Google account. For each of them, Google stores and displays the corresponding IMEI code.
A tech-savvy writer with a knack for finding the latest technology in the market, this is what describes John Carter. With more than 8 years of experience as a journalist, John graduated as an engineer and ventured soon into the world of online journalism. His interest includes gadget reviews, decoding OS errors, hunting information on the latest technology, and so on.











