What is the MAC address or physical address: what it is for and why it is useful.
Each device capable of connecting to the Internet and equipped with a network card, Ethernet or wireless, is equipped with an identifier consisting of 6 octets (6 bytes) called MAC address (or “MAC address”, in Italian).
The MAC address is unique and consists of two parts, with the first 3 bytes that allow you to immediately trace the device’s manufacturer or network card (which is why it is also called the physical address ).
By accessing the router administration panel (usually through the IP 192.168.1.1 or 192.68.0.1 even if it can be different and arbitrarily set by users) and referring to the Connected devices section, you get the list of clients connected via Ethernet cable or WiFi mode.
The same result can be achieved using a free app for Android devices such as Fing.
Fing and the applications of its same category can establish which devices are connected to the local network after scanning it by examining the MAC address’s first three octets.
Try to visit the official list updated by IEEE ( Institute of Electrical and Electronics Engineers ): the first 3 bytes of the MAC address are indicated for each manufacturer.
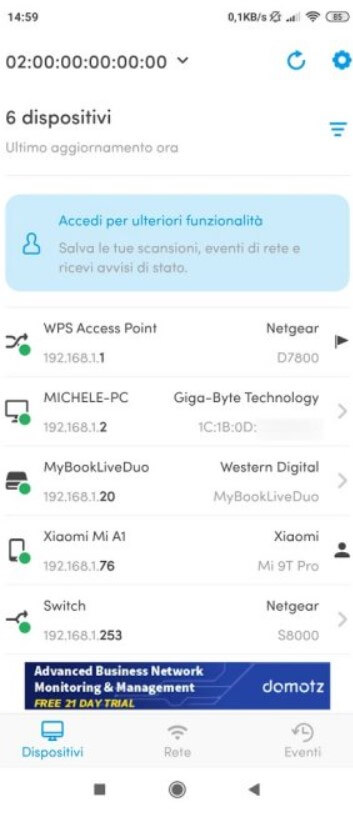
As you can see in the image, Fing has indicated the manufacturer and, in many cases, also the name of the single device by analyzing its specific characteristics (response messages obtained, open ports, identification strings detected, …).
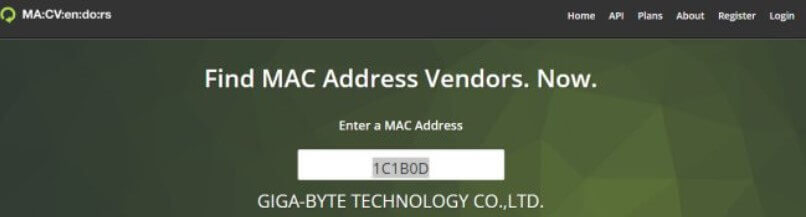
In the image, Fing obviously could not recognize the motherboard model used on the desktop PC, but he nevertheless revealed that it is a GIGABYTE using the MAC address. Looking for the first 3 bytes 1C1B0D in the IEEE list or on MAC Vendors, you can personally verify that the network card manufacturer is, in this case, just the one indicated.
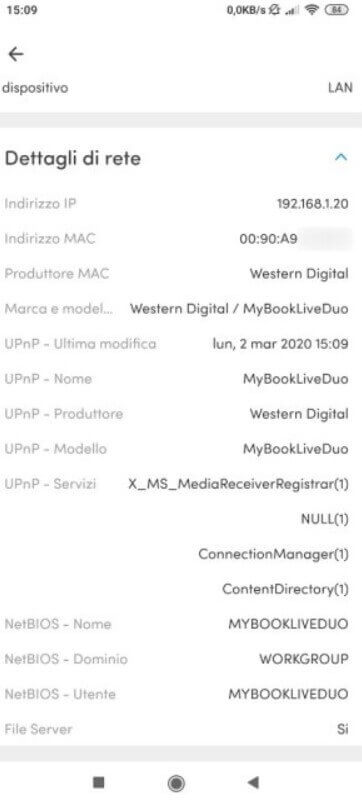
In the case of Fing, to read the MAC addresses of the other devices connected in the local network, just touch their name and refer to the item MAC address.
The network card manufacturer uniquely assigns the next 3 bytes of the MAC address (48 bits) to this device. This means that there are no two or more network cards with the same MAC address on the face of the earth.
From a Windows PC, it is possible to find out the MAC address of the network cards using the ipconfig / all command and reading what is reported under the Physical address.
Then there is a “special” MAC address that is ff: ff: ff: ff: ff: ff, which is used as a broadcast address or to send data to all the network cards of the devices connected to the local network.
What is the MAC address for, and why is it useful
Each device connected to the local network is assigned a private IP address. It may or may not remain the same over time (for example, because it is statically attributed) or change very often.
The MAC address, on the other hand, by its very nature, does not change and remains unchanged over time. In addition to recognizing the devices connected to the local network, the MAC address can also be used to assign static IP addresses on the router side to the client devices. Suppose it is true that any device can be assigned a static private IP address (which therefore remains unchanged) by acting on its interface. In that case, it is possible to take advantage of a particular router function (called IP and MAC binding ).
If you are administering a WiFi network, you can block access to certain devices by setting the restriction at the router or hotspot level. Or, again, if excessive consumption of the network bandwidth by a device is detected, its “freedom of action” can be limited by reducing the amount of data it can transfer in the unit of time.
In any case, an accommodation facility or a commercial establishment should always move the customers’ devices to a guest WiFi network created for this purpose. Unlike the manufacturer claims, not all routers offer perfect isolation between guest networks and the main WiFi.
In the article How to change MAC address on Windows, Linux, and macOS, we have explained how, on the client-side, you could force the modification of the MAC address associated with each network card.
For this reason, for example, controlling access to a WiFi network based on the MAC address makes very little sense. Much better, for commercial entities, to set up an effective captive portal: at the time, we talked about Tanaza, but there are also other solutions.
The so-called de-authentication attack is a very popular mechanism among those who want to force access to a protected WiFi. Even with protected networks using the WPA2 algorithm, it is possible to force devices’ disconnection using their MAC address. The attacker uses the deauthentication attack technique to intercept the 4-way handshake. This activity occurs between the client and the WiFi router when the forcibly disconnected device immediately tries a new connection. The same approach is used by some cybercriminals to force a device to connect to a malicious WiFi hotspot ( evil twin; we talked about it some time ago: Stealing the WiFi password: beware of evil twins ).
Finally, it is important to highlight that the Guarantor for the protection of personal data has also established the MAC address and the public IP address, which is to be considered personal data. Therefore, be careful to inform employees of any MAC address-based monitoring activities within the local network.
A tech-savvy writer with a knack for finding the latest technology in the market, this is what describes John Carter. With more than 8 years of experience as a journalist, John graduated as an engineer and ventured soon into the world of online journalism. His interest includes gadget reviews, decoding OS errors, hunting information on the latest technology, and so on.













