How to encrypt the contents of hard drives and SSD drives with BitLocker: what it is and how it works.
The new general regulation on data protection approved in Europe, better known by the acronym GDPR ( General Data Protection Regulation – EU Regulation 2016/679), is fully adequate, starting from 25 May 2018.
The GDPR requires that data be encrypted, even within company mobile devices, so that the information stored therein is not accessible by unauthorized third parties., even in the event of theft or loss of your laptop, tablet, convertible, or smartphone.
Windows provides a solution to encrypt the data contained in the various external storage media. Many users are used to saving data on USB sticks that they always carry with them. The risk of losing these devices is very high: it is essential that all data held on USB sticks and external hard drives are always encrypted.
BitLocker is a security feature built into Windows that allows you to encrypt the contents of removable drives making the data inaccessible to third parties. We covered this in the article Password-protect your USB stick or removable drives.
BitLocker, however, does not allow you to encrypt only external drives: BitLocker Drive Encryption is a feature offered in the Pro, Ultimate, Enterprise, and Education editions of Windows that will enable you to protect the contents of individual partitions or entire hard drives, including the hard disk or SSD on which the operating system is installed.
What is the TPM chip, and what is it for
TPM ( Trusted Platform Module ) is a chip installed on most modern motherboards used to store cryptographic keys used by the system. Each TPM chip is equipped with a unique cryptographic key pair that makes it uniquely identifiable and an asymmetric encryption engine to encrypt the data.
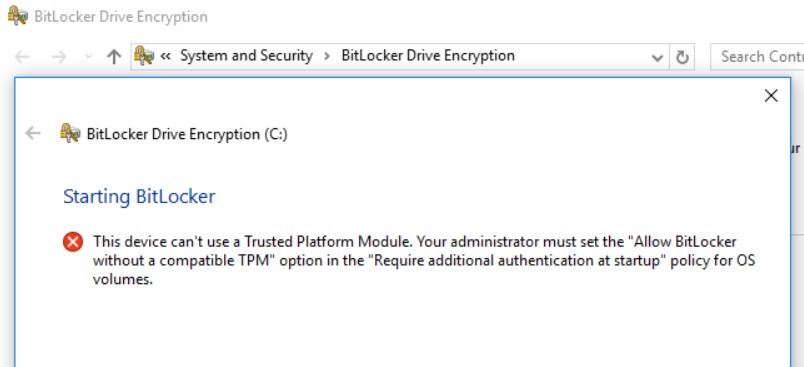
By default, BitLocker requires the use of a version 1.2 TPM chip to function. Otherwise, if you try to enable content encryption, an error message like the one shown in the figure will be indicated.
To check if your device has a TPM chip, press the Windows + R key combination, then type tpm.msc and press Enter.
If you see the message Cannot find a compatible TPM in your computer, it means that your PC does not have the TPM chip or has not been activated in the BIOS / UEFI.
By doing this, on machines equipped with a TPM chip, once the system is restarted and back in Windows, BitLocker can be used to encrypt the contents of the hard drive or SSD.
A reference to the TPM chip also appears in the Windows Device Manager screen, accessible by pressing Windows + R, then type devmgmt.msc . If on the BIOS / UEFI side the use of the TPM chip was already enabled, it is good to check that the use of the same component has not been disabled from the Device Manager window.
Use BitLocker to encrypt drives, even on systems without a TPM chip.
As mentioned, BitLocker requires a version 1.2 TPM chip to work. By applying a change at the system policy level, it is still possible to use BitLocker even on those systems that do not have the TPM chip.
It is undoubtedly a less secure approach than using a hardware component with anti-tampering capabilities but using BitLocker entirely in software mode is better than nothing.
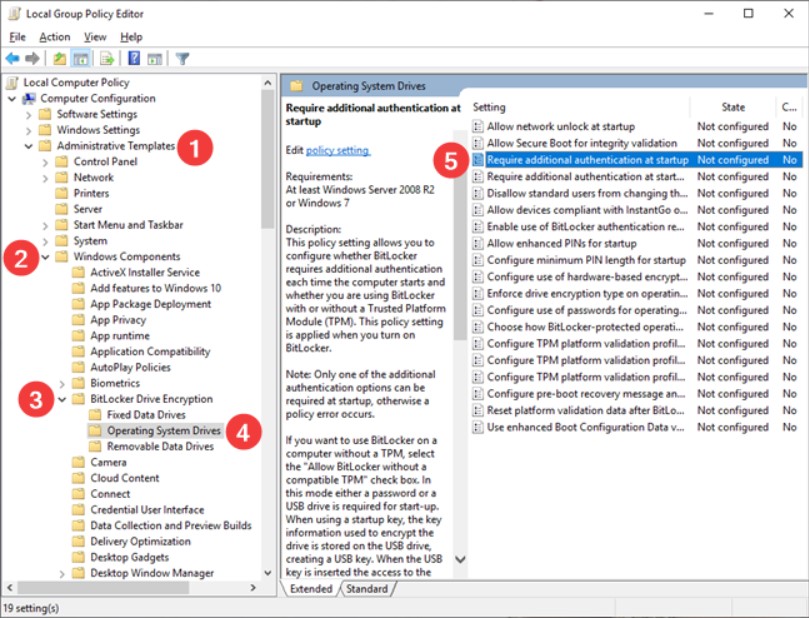
To use BitLocker on machines without TPM, you have to use the Windows + R key combination then type gpedit.msc : Local Group Policy Editor will start.
At this point, it will be enough to go to the sectionPolicies Local Computer, Computer Configuration, Administrative Templates, Windows Components, BitLocker Drive Encryption, Operating System Drives.
By clicking on Require additional authentication at startup in the right panel, you will have to select the Enabled option making sure that the Allow BitLocker without Compatible TPM box is also checked.
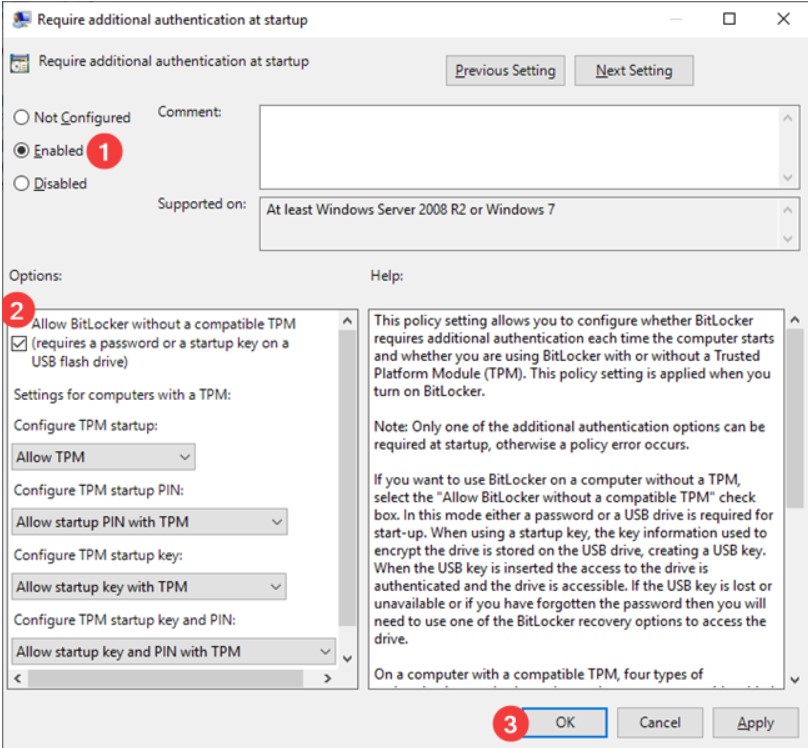
With a click on the OK button, the change will take effect immediately: you will not even have to restart the operating system.
To use BitLocker, you will have to set a personal password, typed each time, or insert a USB key when booting the PC.
Configure BitLocker to protect the contents of the entire drive
BitLocker setup is started by simply typing BitLocker into the operating system search box and choosing Manage BitLocker.
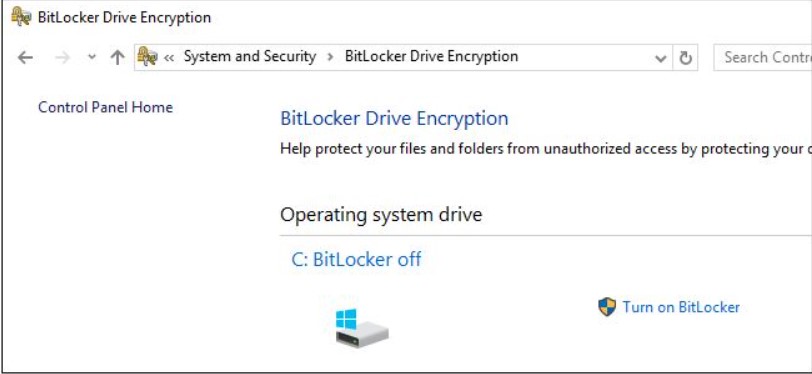
At this point, click on Activate BitLocker, corresponding to each drive you intend to encrypt and follow the step-by-step procedure presented by Windows.
If you have a PC without a TPM version 1.2 chip, BitLocker will immediately ask you to set a password or set a USB key that must always be inserted when the protected machine is started.
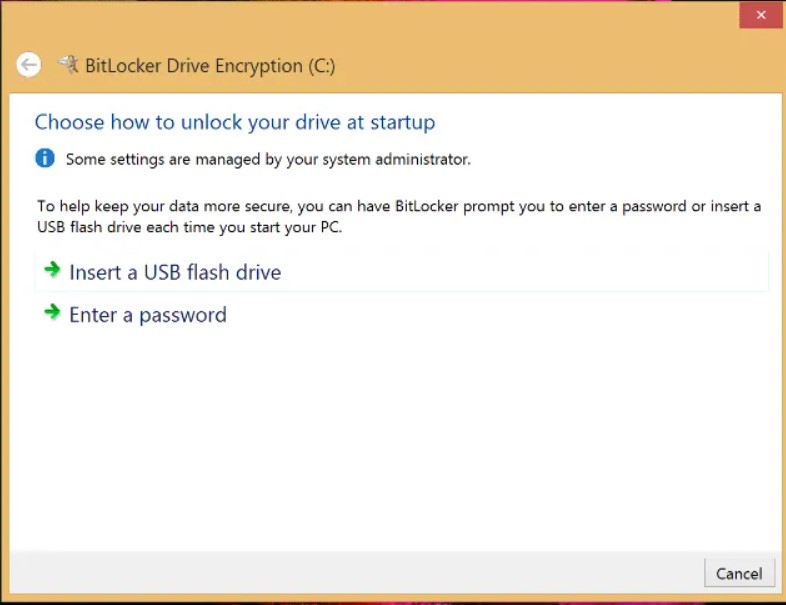
The rest of the procedure is identical to the usual one proposed on systems equipped with TPM chips.
However, system unlocking with a USB startup key can also be configured on systems equipped with a TPM: BitLocker chip, how key recovery and USB unlocking work.
A tech-savvy writer with a knack for finding the latest technology in the market, this is what describes John Carter. With more than 8 years of experience as a journalist, John graduated as an engineer and ventured soon into the world of online journalism. His interest includes gadget reviews, decoding OS errors, hunting information on the latest technology, and so on.