We present some of the best solutions to find the password used when logging into Windows.
Sometimes you may not be able to remember the password to log in to Windows with your user account, or you may need to provide support to third parties to log in even though you have forgotten your password.
There are several approaches to find the login password in Windows. In this article, we are going to summarize the most effective ways, a few of them have already been the subject of previous discussion.
For our part – in the case of passwords for login in Windows – we consider it useless to set up a brute force attack with a tool like Ophcrack that causes inconvenience in the use of rainbow tables. These pre-computed tables collect the hashes of all possible passwords.
Ophcrack allows subsequent attempts, to find the Windows login password. Still, in most cases, if you are dealing with a simple installation of the Microsoft operating system, you can access the desktop and the machine’s contents without much efforts, merely by exploiting some “lightness” of Windows.
1) The Permanent Keys method to find the Windows login password
This is a trick that works with Windows 7, Windows 8.1, and Windows 10 that allows you to access the system without knowing the password used to protect any of the configured user accounts.
Strictly speaking, this method does not allow you to crack the password to log in to Windows, but it does allow you to change the accounts’ password without remembering the one previously set.
The procedure also allows you to create an administrative account, with its desktop, which can access the system content without limitations and also permits you to manage other accounts from the usual Windows interface.
This methods allows you to access the contents of the various folders contained in C: \ Users and modify the system settings without changing the password of any account.
The only problem with this approach is that if the command used to modify an existing user account works perfectly with local user accounts, the traditional ones won’t affect Microsoft user accounts.
Suppose you try to reset the Microsoft account password used to log in to Windows 8.1 or Windows 10 & you receive the error message “the system is not authoritative for the specified account and therefore cannot complete the operation. Retry the operation using the provider associated with this account. If it’s an online provider, use their online site, “and the password gets changed.
However, as mentioned, you can still create a new administrative user account and leverage it to access the Windows system.
The procedure to follow is illustrated in the following articles and has remained substantially unchanged in the case of Windows 7, Windows 8.1, and Windows 10:
All comes down to booting the operating system from the installation media, emergency support, or the advanced boot menu.
From here, accessing the command prompt will simply replace the executable file that calls the Permanent Keys feature(the one that is activated by pressing the SHIFT key five times in Windows) with the one that activates the Command Prompt:
cd windows \ system32
ren sethc.exe sethc.old
copy cmd.exe sethc.exe
Restart the machine when the Windows logon screen appears, click on the Accessibility icon or quickly press the SHIFT key several times, the Prompt will show up the commands.
From here, by typing the following command, you can change the password of any account:
net user account_name_user *
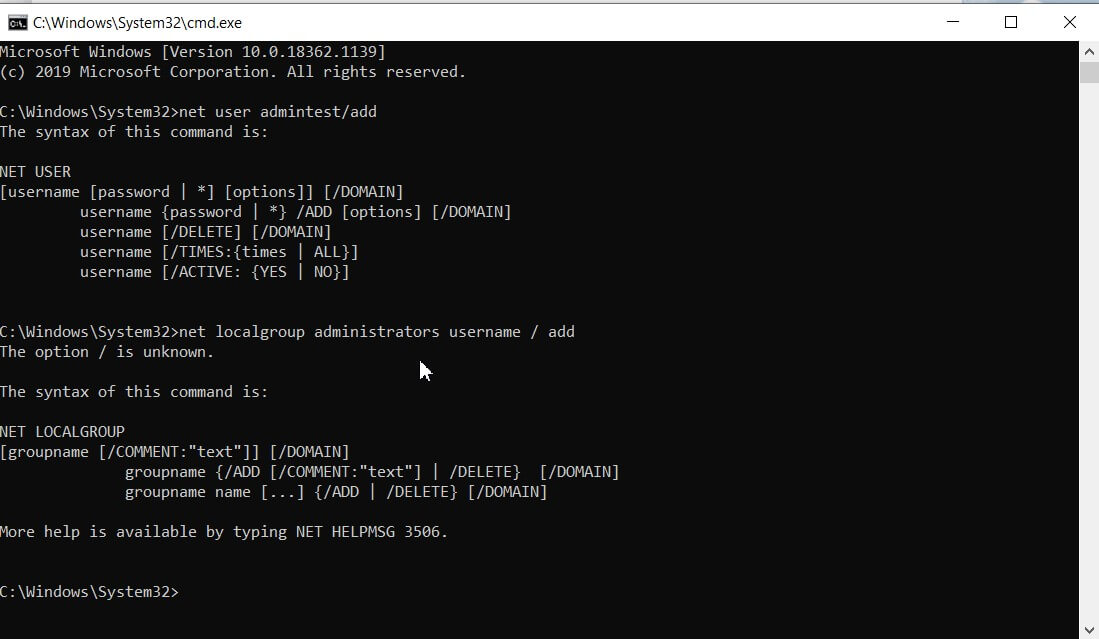
Using the following commands, however, you can create a new administrator account, free to make any changes to the system:
net user username / add
net localgroup administrators username / add
After having done all the necessary interventions, it is possible to delete the administrator account by restarting the system, calling the command prompt with the Accessibility icon (or pressing the SHIFT key several times) when the login screen appears, and then typing the following:
net user / delete user_account_name
2) Using Kon-Boot to find the Windows login password
One of the best software tools to log in to Windows with an existing account without knowing the password is Kon-Boot.
To use Kon-Boot, simply insert the software into a boot stick and boot the system from that medium instead of the hard drive or USB drive as you usually do.
Before proceeding, however, if you are using a machine based on UEFI BIOS, you will need to temporarily disable the Secure Boot feature: Secure Boot and Windows: what is it for and how to disable it.
If the Secure Boot feature is enabled, Kon-Boot will not start because it does not have a recognized and authorized digital signature.
By booting the system from Kon-Boot media, Windows 7, Windows 8.1, or Windows 10 will load normally. The reason behind it is that with Kon-Boot in memory, it will no longer be necessary to type a password to access existing user accounts.
Kon-Boot support applies a temporary “patch” to a Windows kernel function called msv1_0! MsvpPasswordValidate .
Kon-Boot intelligently changes the default value of this function to true so that any password you enter is still granted access to Windows.
When you disconnect the Kon-Boot support and restart the system, everything will be as before, and Windows 7, Windows 8.1, Windows 10 will resume checking the correctness of the passwords entered in the login window.
The good news is that Kon-Boot can login to Windows even for Microsoft user accounts. However, the mechanism only works on Windows 8 and Windows 8.1, and fails for Windows 10.
Kon-Boot is a paid software (the single license costs just over 16 dollars) that is compatible with Windows XP, Windows Server 2003, Windows Vista, Windows Server 2008, Windows 7, Windows 8, Windows 8.1, Windows 10 in versions 32 and 64 bit.
There is also the old free version that only supports the 32-bit versions of Windows XP, Windows Server 2003, Windows Vista, Windows Server 2008, and Windows 7. You can download it.
Once Kon-Boot has loaded, you can still use the “sticky keys” trick seen above and have full access to the system from the Command Prompt window when the Windows logon.
With the following commands, you can manually create a new account with administrator rights:
net user username / add
net localgroup administrators username / add
3) Using Kali Linux to change login passwords in Windows
Another alternative is the Kali Linux distribution, which is downloadable at this address in versions for 32 and 64 bit systems.
After downloading the Kali Linux ISO file, you can insert it into a USB key (which will automatically be made bootable) using a program like Rufus: Rufus, a guide on how to use the program to create bootable media.
Restarting the system from the Kali Linux media, once the Linux distribution has booted up, you will have to open the command prompt and type:
ls / dev / sd *
The next step is to “mount” the contents of the various partitions identified on the disk. Example:
mount / dev / sda1 / mnt
mount / dev / sda2 / mnt
Typing cd mnt && ls should detect the presence of the Windows folder.
The following command will allow you to access the folder containing the hashes of the passwords used to login to Windows and start the chntpw utility:
cd Windows / System32 / config && chntpw -i SAM
By pressing the “1” key, you will communicate your intention to change the Windows user account and password.
The alphanumeric identifier reported in the RID column and corresponding to the account whose password is to be changed must be reported in the Please enter user number (RID) line.
By pressing the “1” key again ( Clear (blank) user password ), chntpw will reset the password associated with the chosen user account.
By typing “q” twice, press “y,” to save the changes.
To conclude, just write cd / && sudo umount / mnt and reboot the machine by removing the Kali Linux boot media.
A tech-savvy writer with a knack for finding the latest technology in the market, this is what describes John Carter. With more than 8 years of experience as a journalist, John graduated as an engineer and ventured soon into the world of online journalism. His interest includes gadget reviews, decoding OS errors, hunting information on the latest technology, and so on.