If the computer has become slow, one of the aspects to ascertain is, first of all, that the system is free from malware and all those components that represent a real ball and chain, as well as a threat to privacy.
Secondly, it is good to check which programs are loaded when the computer starts. If you usually install many applications, likely, multiple executables are automatically loaded when you start your computer, slowing down the system loading process and its normal operation.
One of the most popular tools in the past was HijackThis. But is it still worth using? In our articles dedicated to how to use HijackThis (here is our very old article dating back to 2005: we explained how the program is nothing more than a utility to check which programs they are loaded when Windows starts.
Unfortunately, HijackThis, a software purchased at the time by TrendMicro, has not been updated anymore.
Although it still works today, on 64-bit versions of Windows, it indicates as non-existent ( file missing) system components present on the machine and, at the same time, absolutely legitimate.
Does it still make sense to use HijackThis today? The short answer is “no”.
HijackThis’s main prerogative is that it is a “ready to use” software, capable of generating a list of all the files loaded when the computer starts.
As an alternative to HijackThis you can use some tools compatible with all versions of Windows, even the most recent.
Let’s start by examining the tools that Windows offers to understand which programs are started when the computer is turned on and which can cause the greatest slowdowns.
The tool that almost everyone knows is called MSCONFIG and is bootable in any version of the operating system by pressing the Windows + R key combination and typing in the Open msconfig box.
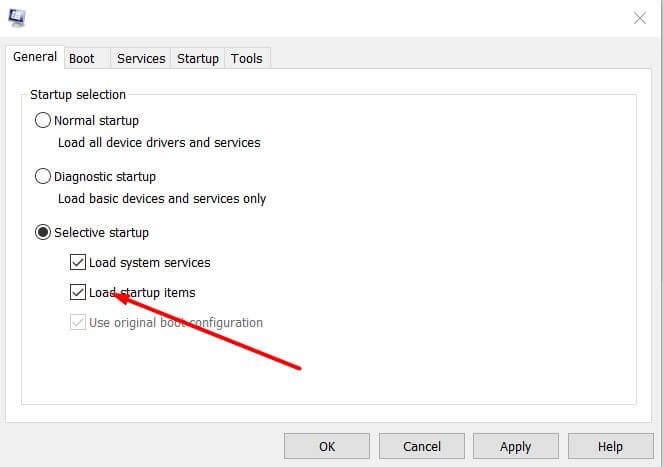
If you remove the checkmark from the Load startup items box from the General tab and restart the system, no items will be loaded when the personal computer is turned on.
Thus, it will be possible to notice the differences in terms of performance between loading with and without the various programs.
However, it should be noted that some elements present in the MSCONFIG Startup tab are essential for the correct functioning of the various devices and some programs. The same applies to system services (listed on the Services tab ).
While in the case of programs ( Startup tab), MSCONFIG provides the complete path, in the case of services, the utility integrated with Windows does not offer this information.
Windows 8.1 offers more useful information. The venerable task manager (Window Task Manager ), which had remained substantially unchanged until the release of Windows 7, is in Windows 8.1 in a completely renewed.
By pressing the key combination CTRL + SHIFT + ESC you can call up the new Task Manager window in Windows 8.1.
By clicking on More details, then on the Startup tab, you will get the list of programs loaded when Windows starts.
In the upper right corner of the window, Windows 8.1 shows the time required for the complete system startup; while clicking with the right mouse button on the header bar, you can activate the display of a series of additional information.
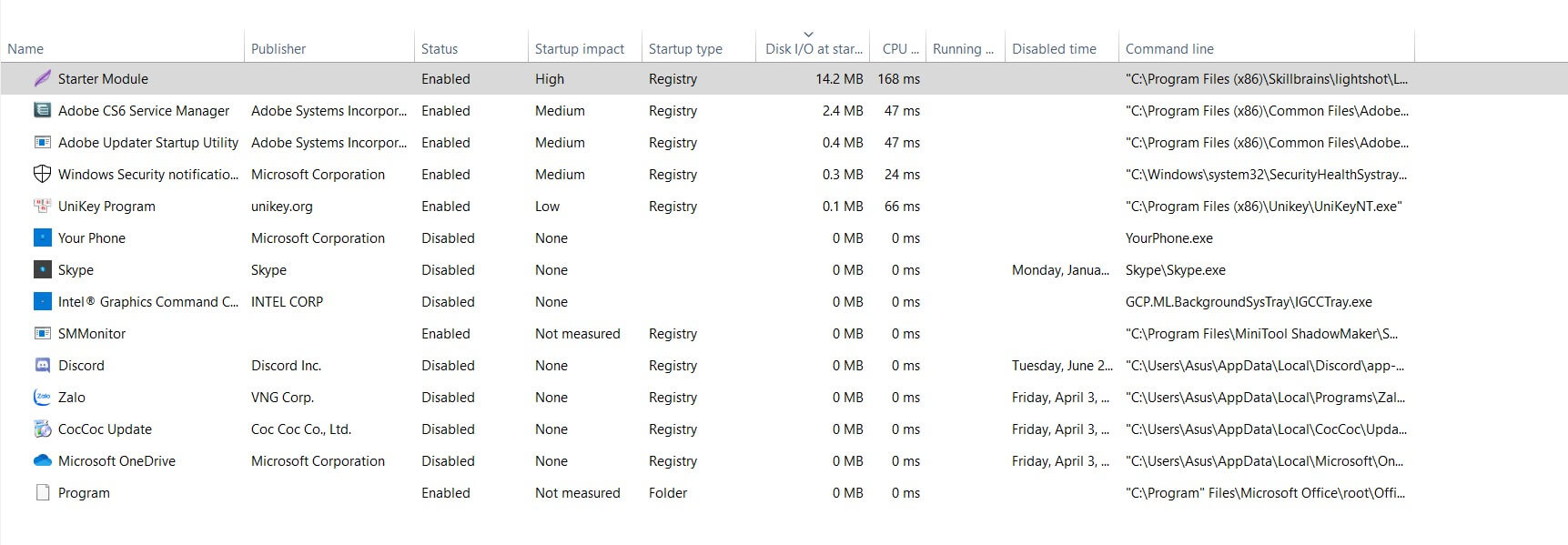
For each program in the automatic start, in addition to the name, the author, the status (enabled or disabled), the startup impact (how much its loading slows down the system startup), the new Windows 8.1 task manager allows you to get information on the type of startup, the amount of data read or written to the disk at startup, the CPU consumption, whether the program is running or not. The last item ( Command Line ) allows you to obtain the name and full path of the file loaded at system startup.
Already an analysis of the elements shown in the Windows 8.1 Task Manager window will allow you to realize which programs can be disabled.
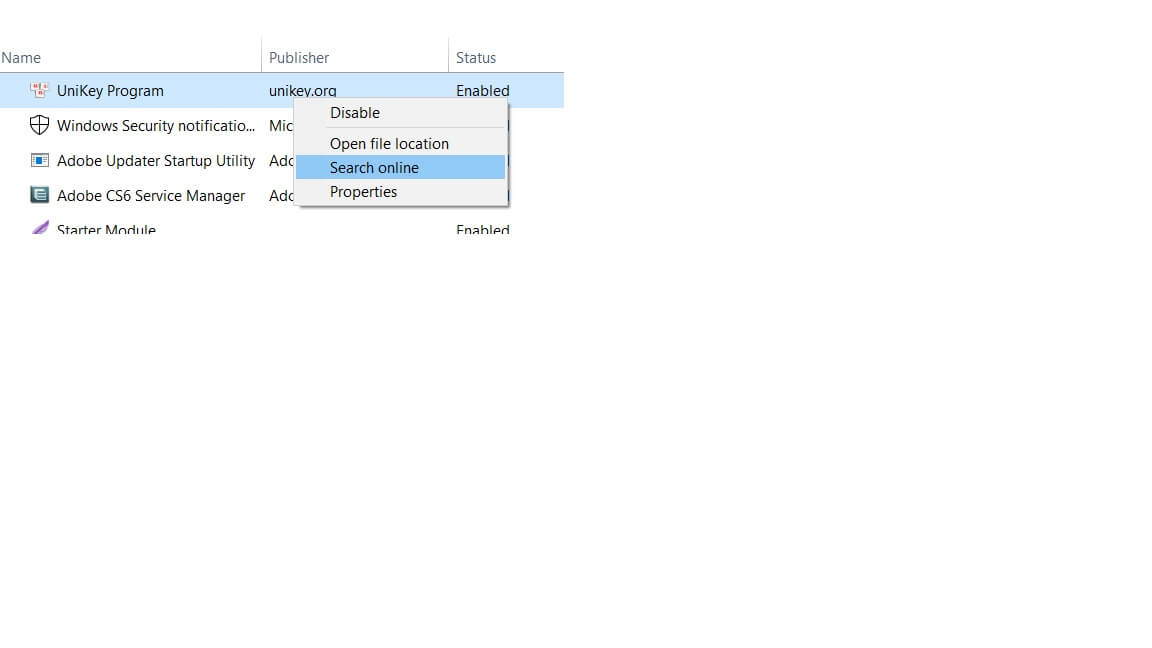
By right-clicking on any item in the list and selecting Search online, a search will be started with the default search engine to establish the identity of the chosen file.
Our advice: use Autoruns
As an alternative to HijackThis you can use the excellent Autoruns available from this tab.
Once run, Autoruns allows you to determine which programs and services are started when the computer is turned on. Regardless of the tools used to configure each program to start automatically, Autoruns’ Everything tab contains the list of all programs and services loaded at Windows startup.
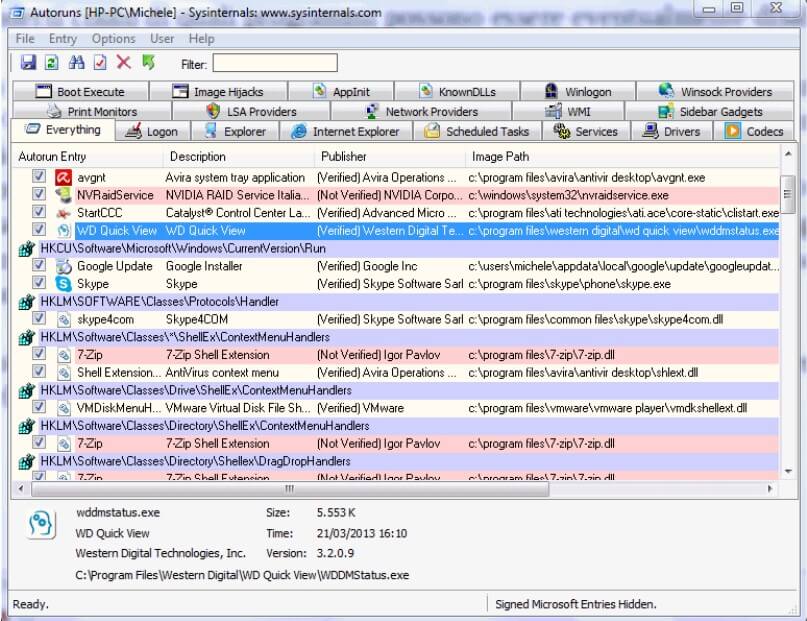
All files that do not have a digital signature are highlighted in pink. These are those elements for which it is not possible to certify the author or the developer company.
For each program, in the Image path column, the corresponding executable file’s complete path is reported.
By clicking on the icon on each item’s left, it is possible to temporarily disable the program while clicking with the right mouse button and choosing Delete; the deletion will take place permanently.
We recommend that you proceed with the possible removal of an entry only after having ascertained that it is useless when starting the computer.
Autoruns also allows you to generate a list of all the elements loaded when Windows starts: to produce it, just click on the File, Save menu and choose, for example, the .TXT format.
Another software to use as an alternative to HijackThis is undoubtedly the excellent CCleaner.
After installing the program or downloading the portable version of CCleaner, by clicking on Tools, Startup, you can check the programs loaded when Windows starts.
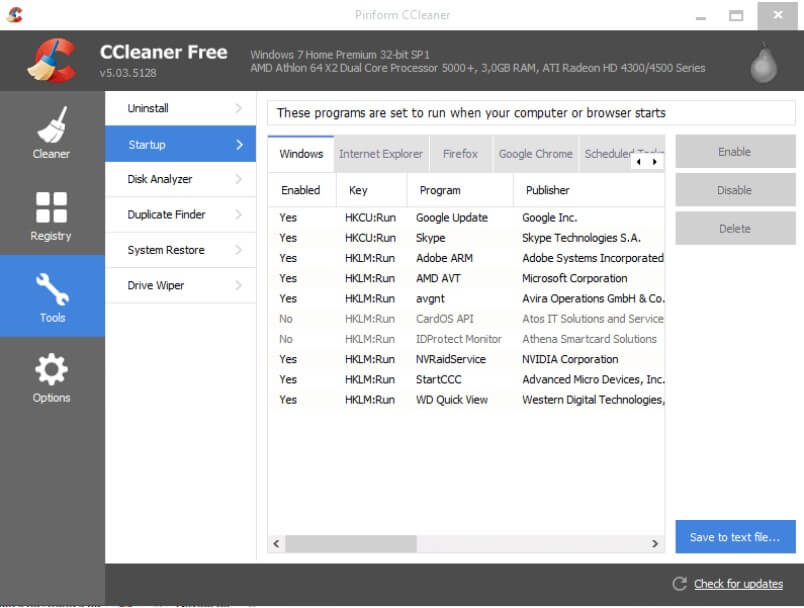
By accessing the various tabs, it is also possible to check plugins and extensions loaded together with the various browsers, interact with the context menu items, and instantly check which activities had been scheduled using the Windows Scheduler.
Verify the identity of programs loaded when Windows starts
If you don’t recognize a program whose loading has been set to automatic when Windows starts, we suggest using a service like Should I Block It.
By typing the file name in the Search box of Should I Block It? you can get complete information about each element’s identity. For each item, you can then know whether the file should be kept or if it can be removed from the list of items loaded when the operating system is started.
In the Search box of Should, I Block It? in addition to the file name, you can also specify – alternatively – the corresponding MD5 or SHA1 signature.
By the same authors, Should I Remove It? instead, is a service that focuses on the elements to be removed.
A tech-savvy writer with a knack for finding the latest technology in the market, this is what describes John Carter. With more than 8 years of experience as a journalist, John graduated as an engineer and ventured soon into the world of online journalism. His interest includes gadget reviews, decoding OS errors, hunting information on the latest technology, and so on.
















